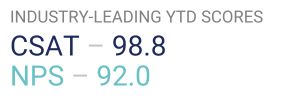
Protect Your Business With Cybersecurity Solutions
Let us help your company fight against cyber threats.
Be prepared for recovery and remediation
Protect your assets from potential threats
Build a strong cybersecurity defense
Today, Every Business Is Vulnerable to Attack
- Do you think cybercriminals don’t find your data and assets valuable?
- Have you punted or pushed cybersecurity down your to-do list only to have your cyber insurance provider bring it to the forefront?
- Are you not sure who to turn to for cybersecurity advice and direction?
If you answered yes to any of these, it’s time to lock down your organization’s cybersecurity so you can rest easy and lower insurance costs.


Don’t Face Cybercriminals Alone
We understand that dealing with cybersecurity can feel like a heavy lift. There’s no denying that every organization today faces a demanding and evolving threat landscape. The good news is there are experts ready to help you put a multi-layered security operation in place. Once you’ve reinforced your security posture you will feel so much better.
- Independent Advisory Services
- 400+ Technology Providers
- Proven “Delta” Process
- Super Support
Managed Detection and Response (MDR)
Managed networks offer built-in security measures that transform how you work. The heir apparent to SIEM, MDR is an outsourced cybersecurity service designed to protect your data and assets even if a threat eludes standard organizational controls. The painful reality is that all organizations are under attack — whether opportunistic or targeted — and the threat landscape is continually changing while the attack surface increases and the perimeter dissolves.
SOC as a Service
Cybersecurity is evolving and complex with many moving parts. Often organizations maintain a lean security posture by design or out of necessity. This approach leaves them open to attack. With the exponential rise in cybercrime, security jobs are the most in-demand careers in technology. This demand has created a talent shortage for businesses. ATC can help you leverage SOC as a service (SOCaaS) to close that talent gap. SOCaaS allows you to maintain high-level security without worrying about the day-to-day details.
Managed Security
Creating and establishing an effective cyber practice is more challenging than ever. It requires tools, talent and time. A managed security solution can quickly establish a security program for you and save you the time and resources it takes to proactively manage it. Managed security solutions include the foundational pieces needed to swiftly get visibility into critical security events while enriching data sets with information from threat intel sources.
- Security information and event management (SIEM)
- Vulnerability scanner
- IDS
- Network forensics
- Endpoint protection
- Behavioral analytics
Unified Threat Management (UTM)
Cybersecurity is complicated, and legacy security systems typically have many different point solutions to cover basic security functions. UTM combines all of the essential managed security needs into a single tool. It’s the tip of the spear on the front lines of your defense.
- Anti-virus
- Anti-spam
- Web filtering
- Content filtering
- Firewall
- Intrusion detection and prevention
Security Information and Event Management (SIEM)
A SIEM solution collects, analyzes and reports on data gathered across an entire IT infrastructure in real-time, including data from networked devices, servers, domain controllers and more.
- Compliance reporting
- Threat intelligence feeds
- Simple integration options
- Data forensics
Featured Provider
You Can’t Afford To Put Your Business at Risk


Not utilizing proven security solutions and services could be putting your organization at unnecessary risk. Experts will tell you that cyberattacks are bound to happen; it’s a matter of when not if. You don’t want to expose your organization by shortchanging cybersecurity measures.
NIST Security Report
Data breaches are becoming increasingly common in today’s ever-evolving technological world. The fiscal cost of data breaches cannot be understated. On average, a data breach costs $9.05 million in the United States alone.
In this report, we dive into the Cyber Security Framework (CSF) developed by the National Institute of Standards and Technology (NIST) and provide you with actionable steps you can take to prevent data breaches, including:
- Building a cross-functional team.
- Creating security project priorities via one-year, three-year and five-year roadmaps.
- Engaging with a trusted advisor.